Search Results for: DNS
Sitting Ducks DNS attacks let hackers hijack over 35,000 domains
Threat actors have hijacked more than 35,000 registered domains in so-called Sitting Ducks attacks that allow claiming a domain without having access to the owner’s account at the DNS provider or registrar. In a Sitting Ducks attack, cybercriminals exploit configuration shortcomings at the registrar level and insufficient ownership verification at DNS providers. Researchers at DNS-focused security vendor Infoblox […]
Botnet fueling residential proxies disrupted in cybercrime crackdown
The Ngioweb botnet, which supplies most of the 35,000 bots in the cybercriminal NSOCKS proxy service, is being disrupted as security companies block traffic to and from the two networks. Following an investigation of more than one year, researchers identified the complete architecture and traffic of the Ngioweb botnet proxy server, which was first observed in […]
Critical bug in EoL D-Link NAS devices now exploited in attacks
Attackers now target a critical severity vulnerability with publicly available exploit code that affects multiple models of end-of-life D-Link network-attached storage (NAS) devices. Tracked as CVE-2024-10914, the command injection vulnerability was found by security researcher Netsecfish, who also shared exploitation details and said that unauthenticated attackers could exploit it to inject arbitrary shell commands by sending […]
Microsoft November 2024 Patch Tuesday fixes 4 zero-days, 89 flaws
Today is Microsoft’s November 2024 Patch Tuesday, which includes security updates for 91 flaws, including four zero-days, two of which are actively exploited. This Patch Tuesday fixed four critical vulnerabilities, which include two remote code execution and two elevation of privileges flaws. The number of bugs in each vulnerability category is listed below: This count […]
D-Link won’t fix critical flaw affecting 60,000 older NAS devices
More than 60,000 D-Link network-attached storage devices that have reached end-of-life are vulnerable to a command injection vulnerability with a publicly available exploit. The flaw, tracked as CVE-2024-10914, has a critical 9.2 severity score and is present in the ‘cgi_user_add’ command where the name parameter is insufficiently sanitized. An unauthenticated attacker could exploit it to inject arbitrary […]
New SteelFox malware hijacks Windows PCs using vulnerable driver
A new malicious package called ‘SteelFox’ mines for cryptocurrency and steals credit card data by using the “bring your own vulnerable driver” technique to get SYSTEM privileges on Windows machines. The malware bundle dropper is distributed through forums and torrent trackers as a crack tool that activates legitimate versions of various software like Foxit PDF Editor, JetBrains and […]
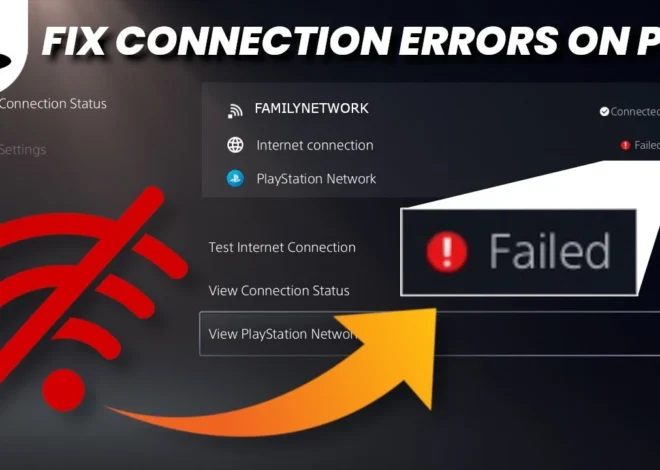
Fix Playstation 5 Connection Issue: How to Resolve ‘Can’t Connect to the Internet’ Error
If you’re having trouble connecting your PS5 to Wi-Fi or the internet, it can be frustrating and can prevent you from enjoying online games, updates, and downloads. There are several possible reasons for this issue, such as incorrect network settings, signal interference, or firmware glitches. If you’re getting the “Can’t Connect To The Internet” message […]
Over 4,000 Adobe Commerce, Magento shops hacked in CosmicSting attacks
Adobe Commerce and Magento online stores are being targeted in “CosmicSting” attacks at an alarming rate, with threat actors hacking approximately 5% of all stores. The CosmicSting vulnerability (CVE-2024-34102) is a critical severity information disclosure flaw; when chained with CVE-2024-2961, a security issue in glibc’s iconv function, an attacker can achieve remote code execution on the […]
CPU Cores Explained: The Key to Better Performance and Multitasking
CPU cores form the heart of modern computer processors. They are the essential components that handle tasks and calculations within a central processing unit (CPU). Each core acts as an independent processor, allowing multiple operations to run simultaneously. This capability enables faster performance and smoother multitasking on computers and devices. The number of cores in a CPU […]
Chrome switching to NIST-approved ML-KEM quantum encryption
Google is updating the post-quantum cryptography used in the Chrome browser to protect against TLS attacks using quantum computers and to mitigate store-now-decrypt-later attacks. The upcoming change will swap Kyber used in hybrid key exchanges to a newer, and slightly modified version, renamed as Module Lattice Key Encapsulation Mechanism (ML-KEM). This change comes roughly five months […]