
New APT CloudSorcerer Malware Hits Russian Target
Cybersecurity researchers have uncovered a new advanced persistent threat (APT) targeting Russian government entities, dubbed CloudSorcerer.
This sophisticated cyberespionage tool, discovered by Kaspersky in May 2024 and discussed in an advisory published by the firm on June 8, is designed for stealth monitoring, data collection and exfiltration, utilizing Microsoft Graph, Yandex Cloud and Dropbox for its command and control (C2) infrastructure.
CloudSorcerer communicates with these cloud services through APIs, using authentication tokens, and employs GitHub as its initial C2 server.
Despite similarities to the CloudWizard APT reported in 2023, CloudSorcerer’s malware code is entirely different, Kaspersky said, suggesting it is a new actor utilizing a similar method of engaging with public cloud services.
Operation and Techniques of CloudSorcerer
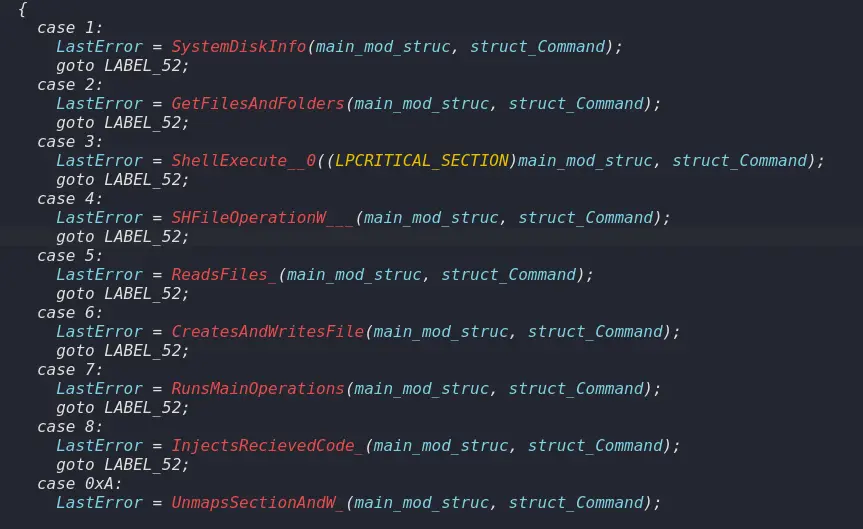
The malware operates by decoding special commands using a hardcoded charcode table and leveraging Microsoft COM object interfaces for malicious activities. It functions as separate modules — communication and data collection — based on the process in which it is executed, all originating from a single executable.
The malware starts by calling the GetModuleFileNameA function to identify the process it is running in. Depending on the process name, it activates specific functions, such as acting as a backdoor module or initiating C2 communication. CloudSorcerer’s shellcode facilitates process migration, utilizing standard methods to identify necessary Windows APIs and injecting code into target processes.
The backdoor module of CloudSorcerer collects system information like computer name, username and system uptime. It sends this data to the C2 module via a named pipe. The main backdoor functionality includes various operations such as gathering information about hard drives, executing shell commands, managing files and injecting shellcode into processes.
Additional advanced functionalities are executed based on specific command IDs, such as creating or deleting tasks, managing services and performing network operations.
The C2 module sets up an initial connection to the C2 server, starting with a GitHub page, and can alternatively use a photo hosting server on my.mail.ru. It decodes hex strings found on these pages to determine which cloud service to use for C2 operations. The malware then interacts with the cloud services, sending and receiving data to and from the backdoor module through asynchronous threads and Windows pipes.
Indicators of a Sophisticated Cyber Espionage Campaign
According to Kaspersky, the infrastructure used by CloudSorcerer indicates a well-planned cyberespionage campaign. The GitHub page, created on May 7, 2024, and the my.mail.ru photo album both contain encoded strings essential for the malware’s operation.
“The malware’s ability to dynamically adapt its behavior based on the process it is running in, coupled with its use of complex inter-process communication through Windows pipes, further highlights its sophistication,” reads the advisory.
“While there are similarities in modus operandi to the previously reported CloudWizard APT, the significant differences in code and functionality suggest that CloudSorcerer is likely a new actor, possibly inspired by previous techniques but developing its own unique tools.”



