
Mitel MiCollab zero-day flaw gets proof-of-concept exploit
Researchers have uncovered an arbitrary file read zero-day in the Mitel MiCollab collaboration platform, allowing attackers to access files on a server’s filesystem.
Mitel MiCollab is an enterprise collaboration platform that consolidates various communication tools into a single application, offering voice and video calling, messaging, presence information, audio conferencing, mobility support, and team collaboration functionalities.
It’s utilized by various organizations, including large corporations, small to medium-sized enterprises, and companies operating on a remote or hybrid workforce model.
The latest vulnerability in the product was discovered by researchers at watchTowr, who, despite having reported to the vendor since August, it remains unfixed after 90 days of being disclosed and waiting for a patch.
“watchTowr contacted Mitel on August 26 about the new vulnerability. Mitel informed watchTowr of plans to patch the first week of December 2024. At the time of publishing, there has been no update on the Mitel Security Advisory page.” explained a watchTowr report published today.
Looking into past flaws to uncover a new one
The latest zero-day, which does not have a CVE identifier assigned to it yet, was discovered while investigating previously reported vulnerabilities in MiCollab, experimenting with path traversal and input manipulation techniques.
Specifically, the researchers were investigating CVE-2024-35286, an SQL injection flaw that Mitel fixed on May 23, and CVE-2024-41713, an authentication bypass issue addressed by the vendor on October 9.
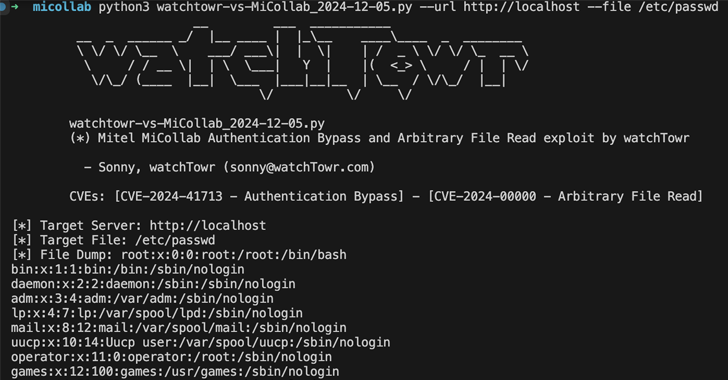
The previously undocumented flaw was discovered while probing the ‘ReconcileWizard’ servlet, performing injections of a path traversal string (../../../) into the ‘reportName’ parameter of an XML-based API request.
This resulted in the researchers being able to access sensitive files such as ‘/etc/passwd,’ which contain sensitive information about the accounts on a system.
A proof-of-concept on how to exploit the flaw was published as part of watchTowr’s writeup.
Though technically less critical than the other two vulnerabilities, the zero-day remains a significant threat as it allows unauthorized users to access sensitive system files.
Also, MiCollab has been targeted by threat actors again in the recent past, so ignoring this risk isn’t prudent.
Defense recommendations
Since the vulnerability is not fixed yet, organizations using MiCollab remain exposed and should implement mitigations immediately.
Measures to consider include:
- Limit access to the MiCollab server to trusted IP ranges or internal networks only.
- Implement firewall rules to prevent unauthorized external access to the application.
- Monitor logs for suspicious activity targeting the ReconcileWizard servlet or path traversal patterns.
- Monitor for unexpected access to sensitive files or configuration data.
- If feasible, disable or restrict access to the ReconcileWizard servlet.
Ultimately, users should ensure that they use the latest version of Mitel MiCollab, which, although it does not address the zero-day flaw, offers protection against other critical flaws discovered recently.



