
Russian cyber spies hide behind other hackers to target Ukraine
Russian cyber-espionage group Turla, aka “Secret Blizzard,” is utilizing other threat actors’ infrastructure to target Ukrainian military devices connected via Starlink.
Microsoft and Lumen recently exposed how the nation-state actor, who is linked to Russia’s Federal Security Service (FSB), is hijacking and using malware and servers of the Pakistani threat actor Storm-0156.
Microsoft released another report today focusing on separate Turla operations between March and April 2024, targeting devices in Ukraine used in military operations.
In the latest campaign, Turla utilized the infrastructure for the Amadey botnet and another Russian hacking group known as “Storm-1837.” This infrastructure was used to deploy Turla’s custom malware families, including Tavdig and KazuarV2, on Ukrainian systems.
Microsoft is unsure whether Turla hijacked Amadey or purchased access to the botnet, but the campaign constitutes another example of the particular threat actor hiding behind other hacker groups.
“Microsoft assesses that Secret Blizzard either used the Amadey malware as a service (MaaS) or accessed the Amadey command-and-control (C2) panels surreptitiously to download a PowerShell dropper on target devices,” explains Microsoft.
“The PowerShell dropper contained a Base64-encoded Amadey payload appended by code that invoked a request to Secret Blizzard C2 infrastructure.”
Overview of Turla attacks in Ukraine
Turla attacks in Ukraine begin with phishing emails carrying malicious attachments, Storm-1837 backdoors, or the Amadey botnet, used for payload deployment on infected devices.
Amadey is a malware botnet that has been used for initial access and payload delivery since 2018. At one point, it was used by LockBit affiliates as a precursor to encryptors being deployed on networks.
The versatile malware is primarily used to act as a malware dropped, and in the case of Turla, it’s used for deploying custom reconnaissance tools on compromised devices and to download PowerShell droppers that load the threat group’s custom malware, Tavdig (“rastls.dll”).
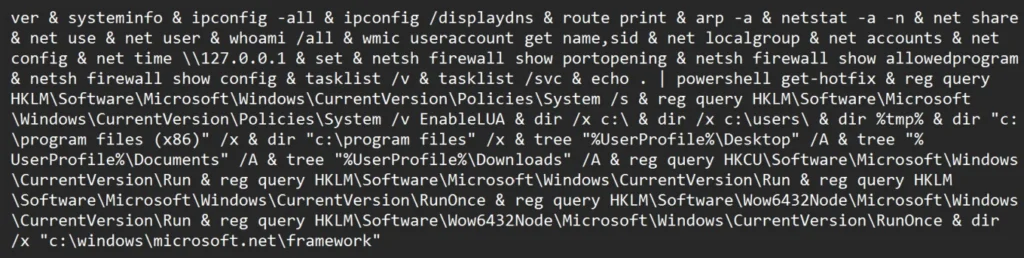
Microsoft explains that the hackers use the reconnaissance info provided by the dropped batch file to identify high-priority targets such as military devices connected to Starlink internet systems.
“Microsoft observed Secret Blizzard downloading their custom reconnaissance or survey tool,” Microsoft explained in the report.
“This tool was selectively deployed to devices of further interest by the threat actor—for example, devices egressing from STARLINK IP addresses, a common signature of Ukrainian front-line military devices.”
Presumably, Starlink devices were targeted to gather intelligence on front-line military activities, aligning with Turla’s role at the FSB.
Microsoft’s report also links Turla with another Russian threat actor known as Storm-1837, who Redmond says has in the past focused on devices used by Ukrainian drone operators
According to Microsoft, Turla was seen utilizing Storm-1837’s Power-Shell backdoor named ‘Cookbox,’ which Storm-1837 deployed in Ukraine in January 2024 by exploiting the WinRAR flaw CVE-2023-38831.
Turla’s custom malware families were later deployed on those systems, indicating that Storm-1837 was either hijacked or worked with Turla to deliver their payloads.
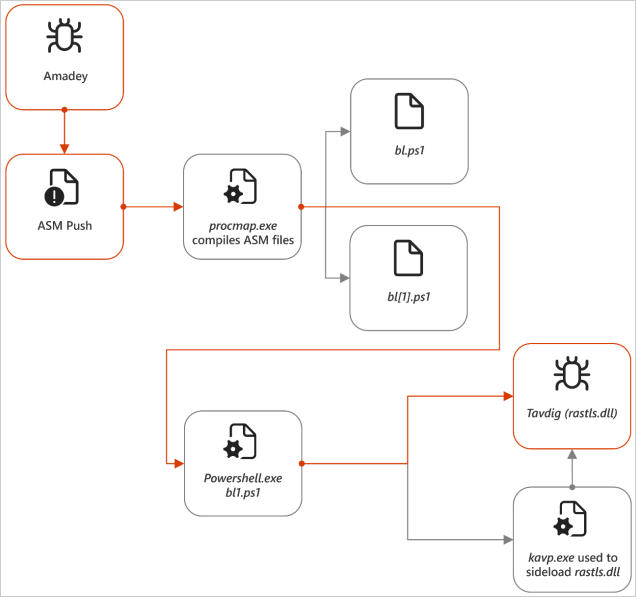
Tavdig and KazuarV2 malware
Tavdig and KazuarV2 are key components of Turla’s malware arsenal, playing distinct but complementary roles in their latest espionage campaign.
Tavdig is a lightweight, modular backdoor designed to establish an initial foothold, conduct surveillance, and deploy additional payloads.
It can collect information like user credentials, network configurations, and installed software, and it can also perform registry modifications and create scheduled tasks for persistence.
One of the tools Tavdig loads on compromised devices is KazuarV2, Turla’s more advanced, stealthy backdoor, designed for long-term intelligence collection, command execution, and data exfiltration.
KazuarV2 is typically injected into legitimate system processes like ‘explorer.exe’ or ‘opera.exe,’ to evade detection and then sends and receive data and commands from its command and control (C2).
Microsoft notes that KazuarV2 is a modular malware, so it can be extended with additional plugins as required, adapting to specific espionage needs.
Defenders are recommended to check Microsoft’s proposed mitigations and hunting queries in the report, which cover this particular Turla operation and the group’s broader activities.



