
New fake Ledger data breach emails try to steal crypto wallets
A new Ledger phishing campaign is underway that pretends to be a data breach notification asking you to verify your recovery phrase, which is then stolen and used to steal your cryptocurrency.
Ledger is a hardware cryptocurrency wallet that allows you to store, manage, and sell cryptocurrency. The funds in these wallets are secured using 24-word recovery phrases or 12 and 18-word phrases generated by other wallets.
Anyone who knows your Ledger recovery phrase can use it to access the funds within the wallet. Therefore, recovery phrases must always be kept offline and never shared with anyone to prevent cryptocurrency funds from being stolen.
Fake data breach notifications
Ledger has long been a target of phishing campaigns that attempt to steal users’ recovery phrases or push fake Ledger Live software to steal information. These campaigns became significantly worse after Ledger suffered a data breach in 2020 that exposed its customers’ names, addresses, phone numbers, and email addresses.
However, over the past few days, multiple people have notified GeekFeed or shared on X that they received a Ledger phishing email that pretends to be a new data breach notification.
The phishing emails have the subject of “Security Alert: Data Breach May Expose Your Recovery Phrase” and appear to be from “Ledger <support@ledger.com”. However, they are actually sent through the SendGrid email marketing platform.
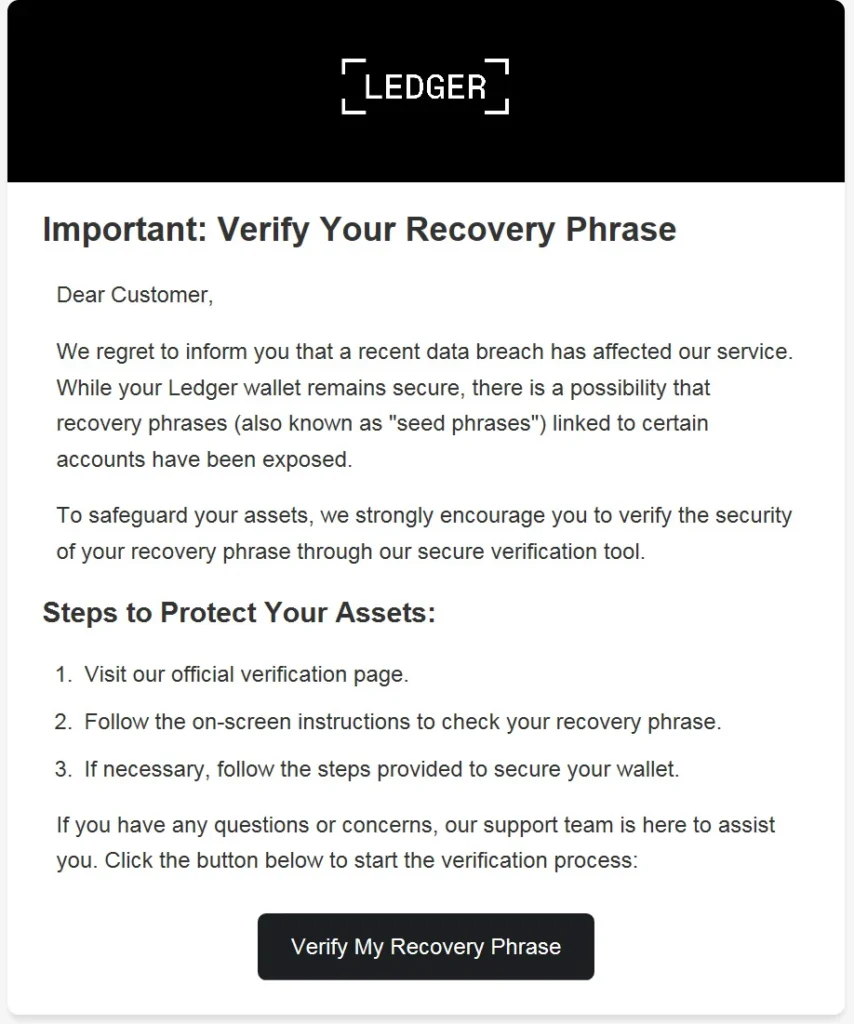
The phishing emails claim that Ledger suffered a data breach and that some recovery phrases have been exposed. The email then goes on to say that the user must verify their recovery phrase on Ledger’s official verification page.
“We regret to inform you that a recent data breach has affected our service. While your Ledger wallet remains secure, there is a possibility that recovery phrases (also known as “seed phrases”) linked to certain accounts have been exposed,” reads the phishing email.
“To safeguard your assets, we strongly encourage you to verify the security of your recovery phrase through our secure verification tool.”
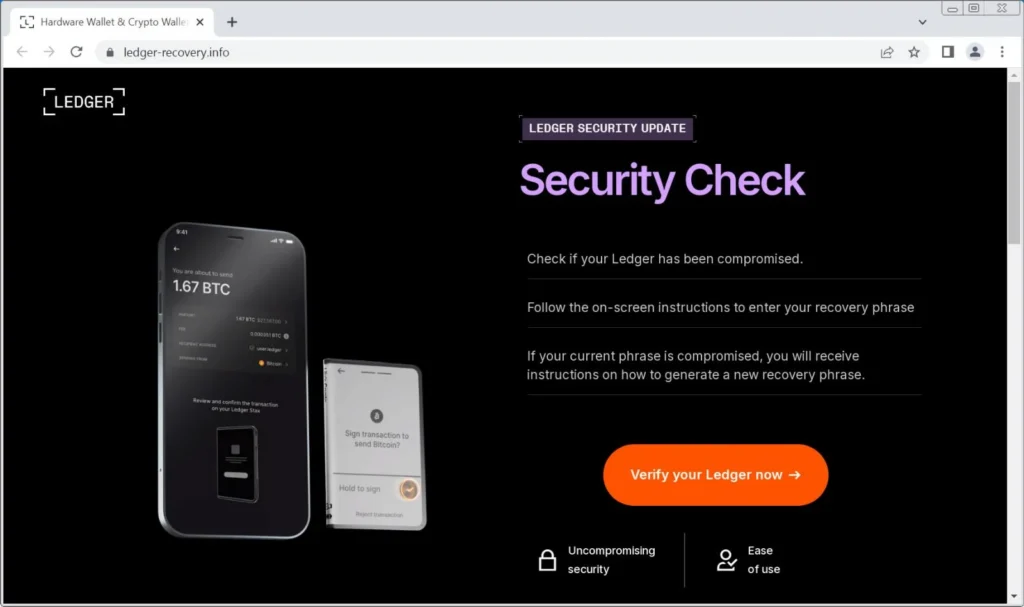
Clicking the “Verify My Recovery Phrase” button brings you to an Amazon AWS website at “https://product-ledg.s3.us-west-1.amazonaws[.]com/recover.html” that then redirects users to a phishing page at “ledger-recovery[.]info”.
The ledger-recovery[.]info domain was registered on December 15th, 2024.
This website pretends to be a Ledger site that asks you to perform a security check to see if your recovery phrase is compromised, as shown below.
Clicking the “Verify your Ledger now” brings up another page asking you to enter your 12, 18, or 24-word Ledger recovery phrase.
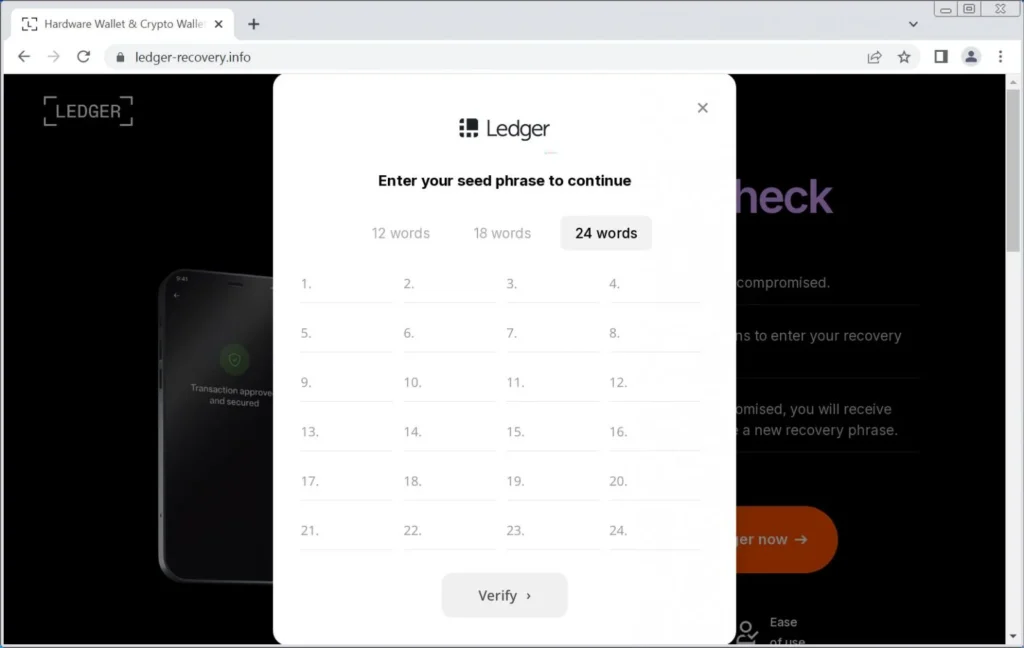
As you enter each word, the phishing page will check if the word is one of 2,048 valid words that can be entered as part of a recovery phrase. If a word not on the list is entered, it will be shown with a line through it.
As you enter each word, the phishing page will send all of the entered recovery words to the site’s backend to store them on the server.
GeekFeed was told that no matter what recovery phrase you enter, it will always state that it was invalid. It is believed this being done so that targets enter the phrase multiple times, allowing the phishing page to verify that the correct words are being entered.
Other people have also shared other Ledger phishing emails sent out recently, including one that pretends to be a new firmware update. It, too, attempts to steal users’ recovery phrases.
Armed with the recovery phrase, the attackers can gain full access to your cryptocurrency funds and steal them.
What should Ledger owners do?
First and foremost, never enter your recovery phrase or secret passphrase in any app or website. Recovery phrases should only be entered directly on the Ledger device you are trying to recover.
As it is easy to create lookalike domains that impersonate legitimate sites, when it comes to cryptocurrency and financial assets, always type the domain you’re trying to reach into your browser rather than relying on links in emails. This way, you know you are going to ledger.com rather than a site impersonating it.
Finally, disregard any emails claiming to be from Ledger stating that you were affected by a recent data breach or asking you to verify your recovery phrase.
Ledger will never ask you for your recovery phrase, and as previously said, it should never be shared with anyone else.



