
Microsoft Teams phishing attack alerts coming to everyone next month
Microsoft reminded Microsoft 365 admins that its new brand impersonation protection feature for Teams Chat will be available for all customers by mid-February 2025.
Once enabled, it will display alerts when detecting phishing attacks targeting organizations that have enabled external Teams access (which allows threat actors to message any user from external domains).
The company first announced that it was working on defenses against Teams brand impersonation in late October 2024 (when it added this initiative to the Microsoft 365 roadmap), and it began rolling it out to users almost one month later, in mid-November.
While the initial rollout timeline estimated it would reach general availability in mid-January, the company said a Microsoft 365 message center advisory updated on Friday that it would be completed in mid-February and enabled by default with no admin configuration needed.
“This rollout will happen automatically by the specified date with no admin action required before the rollout. You may want to update any relevant documentation,” Microsoft said. “We recommend that you educate your users on what the new high-risk Accept/Block screen means and remind users to proceed with caution.”
Various threat actors, including state-sponsored threat actors, access brokers, and ransomware gangs posing as IT support, have used brand impersonation in phishing and malware attacks.
For example, Russian state-sponsored hackers known as Midnight Blizzard have previously targeted government employees in Teams phishing attacks that impersonated Microsoft tech support.
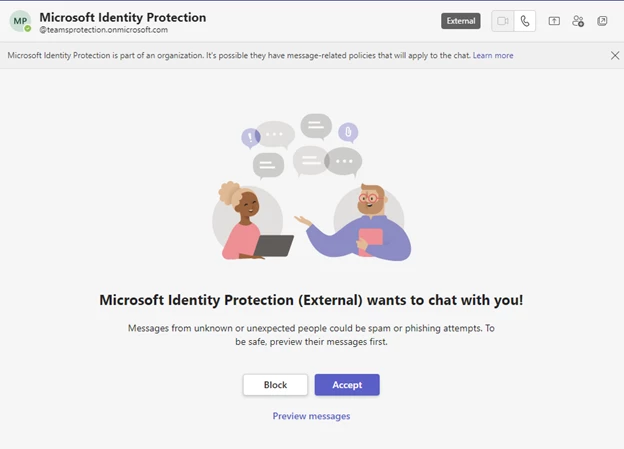
“If your organization enables Teams external access, we will check for potential impersonation activity when your user receives a message from an external sender for the first time,” Microsoft added.
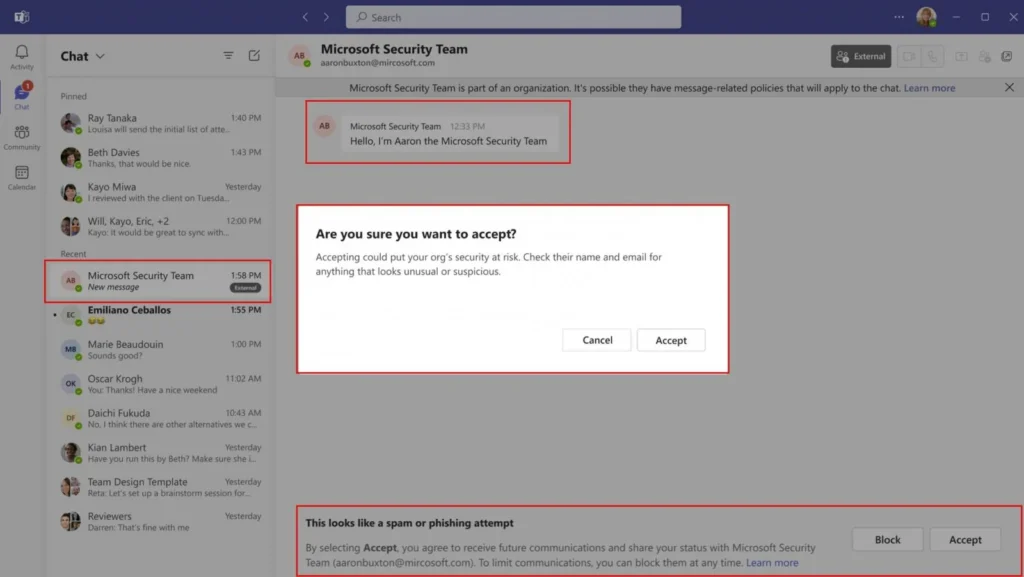
“Your users will see a high-risk warning in the Accept/Block flow if we think there is potential impersonation risk, and users must preview the message before they can choose to Accept or block. If users choose to accept, we will prompt them again with potential risk before proceeding with Accept.”
The security checks that detect impersonation attempts will be automatic and do not require admin configuration. Admins can also check the audit log for any detected phishing attacks that have used this tactic.
Until the feature rolls out, the recommended action for those who use Microsoft Teams and don’t need to maintain regular communication with external tenants is to disable the feature from “Microsoft Teams Admin Center > External Access.”
If external communication channels are required, admins can also add specific domains to an allow list to lower the risk of exploitation.
Microsoft announced last year that “Teams has grown to serve over 320 million monthly active users across 181 markets and 44 languages.”



