
Dozens of solar inverter flaws could be exploited to attack power grids
Dozens of vulnerabilities in products from three leading makers of solar inverters, Sungrow, Growatt, and SMA, could be exploited to control devices or execute code remotely on the vendor’s cloud platform.
The potential impact of the security problems has been assessed as severe because they could be used in attacks that could at least influence grid stability, and affect user privacy.
In a grimmer scenario, the vulnerabilities could be exploited to disrupt or damage power grids by creating an imbalance between power generation and demand.
Hijacking PV inverters
Security researchers at Vedere Labs, the cybersecurity research arm of network security company Forescout, found 46 vulnerabilities in solar inverters from Sungrow, Growatt, and SMA – three of the top six manufacturers in the world.
The potential impact of some of the vulnerabilities is significant as they could lead to unauthorized access to resources in cloud platforms, remote code execution (RCE), device takeover, information disclosure, physical damage, and denial of service.
Of the 46 issues discovered, only one, CVE-2025-0731, impacts SMA products. An attacker could use it to achieve remote code execution by uploading .ASPX files that would be executed by the web server at sunnyportal.com – the company’s platform for monitoring photovoltaic (PV) systems.
In a report today, Forescout describes how an attacker could use the newly disclosed vulnerabilities to hijack Growatt and Sungrow inverters.
The researchers say that taking control of Growatt inverters is easier “because it can be achieved via the cloud backend only.”
However, they note that although control over the device is not complete, a threat actor has access to the inverter’s configuration parameters and can modify them.
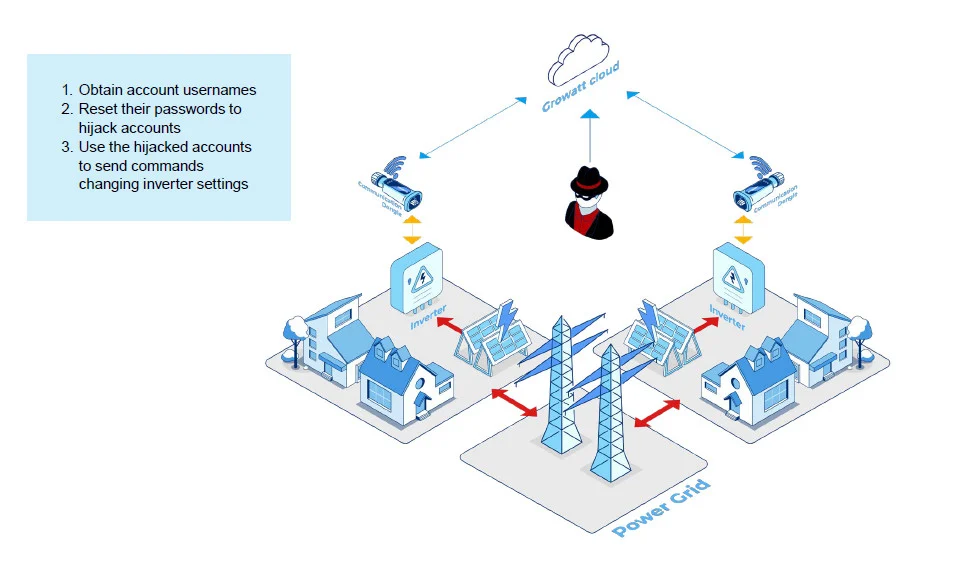
An attacker could enumerate without authentication usernames from an exposed Growatt API and then take over accounts by exploiting two IDOR (insecure direct object references) vulnerabilities, or steal credentials via JavaScript injection by leveraging two stored XSS issues.
With this type of access, a threat actor “can perform operations on the connected inverter devices, such as switching it on or off.”
The researchers say that taking control of Sungrow inverters is “slightly more complex” because it involves multiple vulnerable components of the vendor’s architecture:
- An attacker can harvest communication dongle serial numbers from the manufacturer’s backend through various IDORs such as CVE-2024-50685, CVE-2024-50693, and CVE-2024-50686.
- The attacker can use the hard-coded MQTT credentials (CVE-2024-50692) to publish messages for an arbitrary inverter communication dongle by putting the correct serial number in the topic.
- The attacker can exploit one of the stack overflow vulnerabilities CVE-2024-50694, CVE-2024-50695, or CVE-2024-50698 (all of them critical) by publishing crafted messages that lead to remote code execution on communication dongles connected to the inverter.
The two attack scenarios above consider only one residential and one commercial inverter but an attacker could follow the same steps to obtain serial numbers of accounts for a fleet of managed devices.
With control over an entire fleet of inverters, an attack on a power grid could be amplified to dangerous levels.
“Each inverter can modulate its power generation within the range permitted by current PV panel production levels. The combined effect of the hijacked inverters produces a large effect on power generation in the grid” – Forescout Vedere Labs
An adversary could obtain a significantly more damaging effect by controlling the hijacked devices as a botnet in a coordinated attack to reduce PV inverters’ power generation during peak production hours, thus influencing the load on the grid.
The researchers explain that this is achieved by “modulating the power generation of inverters inversely to the attempts of the primary control.”
“When the primary control decreases the load at its maximum capacity, the attack will reduce all its load immediately, forcing the primary control to raise the load in the system followed by an immediate increase of the load by the attack” – Forescout Vedere Labs
Apart from disrupting a power grid, the disclosed vulnerabilities can also be exploited in scenarios that impact user privacy, hijacking smart devices in the house that may be controlled through the vendor’s cloud platform, or even ransomware attacks by holding the devices hostage until a ransom is paid.
The researchers say that Sungrow and SMA patched all reported vulnerabilities, the former asking for confirmation that their fix addressed the issues and showing a willingness to improve their security posture.
Growatt also fixed the problems and released the patches in a way that should not involve any modification in the inverters, the researchers said.
The report from Forescout’s Vedere Labs dives deeper in the technical details of the vulnerabilities and is available here [PDF].



