
CISA confirms critical Cleo bug exploitation in ransomware attacks
CISA confirmed today that a critical security vulnerability in Cleo Harmony, VLTrader, and LexiCom file transfer software is being exploited in ransomware attacks.
This flaw (tracked as CVE-2024-50623 and impacting all versions before version 5.8.0.21) enables unauthenticated attackers to gain remote code execution on vulnerable servers exposed online.
Cleo released security updates to fix it in October and warned all customers to “immediately upgrade instances” to additional potential attack vectors.
The company has not disclosed that CVE-2024-50623 was targeted in the wild; however, on Friday, CISA added the security bug to its catalog of known exploited vulnerabilities, tagging it as being used in ransomware campaigns.
Following its addition to the KEV catalog, U.S. federal agencies must secure their networks against attacks by applying by January 3, as required by the binding operational directive (BOD 22-01) issued in November 2021.
While the cybersecurity agency didn’t provide any other information regarding the ransomware campaign targeting Cleo servers left vulnerable to CVE-2024-50623 exploits, these attacks are uncannily similar to previous Clop data theft attacks that exploited zero-days in MOVEit Transfer, GoAnywhere MFT, and Accellion FTA in recent years.
Some also believe the flaw was exploited by the Termite ransomware operation. However, it is believed that this link was only made because Blue Yonder had an exposed Cleo software server, and they were breached in a cyberattack claimed by the ransomware gang.
Cleo zero-day also actively exploited
As Huntress security researchers first discovered ten days ago, fully patched Cleo servers were still being compromised, likely using a CVE-2024-50623 bypass (which has yet to receive a CVE ID) that enables attackers to import and execute arbitrary PowerShell or bash commands by exploiting the default Autorun folder settings.
Cleo has now released patches to fix this actively exploited zero-day bug and urged customers to upgrade to version 5.8.0.24 as soon as possible to secure Internet-exposed servers from breach attempts.
“After applying the patch, errors are logged for any files found at startup related to this exploit, and those files are removed,” the company added.
Admins who can’t immediately upgrade are advised to disable the Autorun feature by clearing out the Autorun directory from the System Options to reduce the attack surface.
As Rapid7 found while investigating the zero-day attacks, threat actors exploited the zero-day to drop a Java Archive (JAR) payload [VirusTotal] part of a larger Java-based post-exploitation framework.
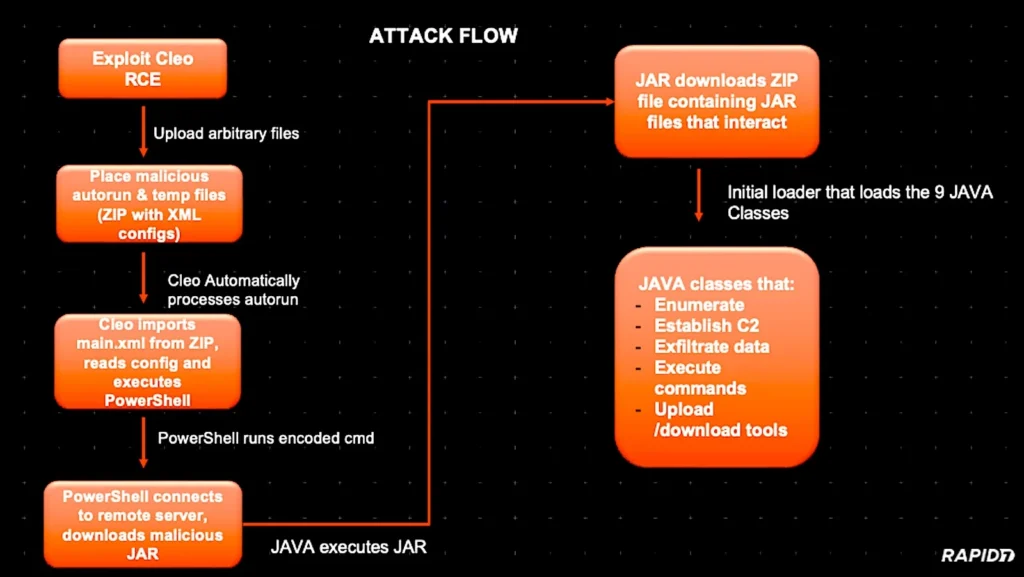
Huntress, who also analyzed the malware and named it Malichus, said it only found it deployed on Windows devices, although it also comes with Linux support.
According to Binary Defense ARC Labs, another cybersecurity firm that looked into the ongoing attacks, malware operators can use Malichus for file transfers, command execution, and network communication.
So far, Huntress has discovered at least two dozen companies whose Cleo servers were compromised and said there are likely other potential victims. Sophos’ MDR and Labs teams have also found indicators of compromise on over 50 Cleo hosts.
Cleo spokespersons were not immediately available when contacted by GeekFeed earlier today to confirm that the CVE-2024-50623 flaw was exploited in attacks as a zero-day.



