
Chinese hackers use Visual Studio Code tunnels for remote access
Chinese hackers targeting large IT service providers in Southern Europe were seen abusing Visual Studio Code (VSCode) tunnels to maintain persistent remote access to compromised systems.
VSCode tunnels are part of Microsoft’s Remote Development feature, which enables developers to securely access and work on remote systems via Visual Studio Code. Developers can also execute command and access the file system of remote devices, making it a powerful development tool.
The tunnels are established using Microsoft Azure infrastructure, with executables signed by Microsoft, providing trustworthy access.
This rare tactic of abusing a legitimate Microsoft system to maintain persistent backdoor access to systems was observed by SentinelLabs and Tinexta Cyber, who dub the campaign ‘Operation Digital Eye,’ which took place between June and July 2024.
The researchers detected and blocked the activities in their early stages but shared the details in a report published today to raise awareness about this new APT tactic.
Evidence weakly points to STORM-0866 or Sandman APT, but the exact threat actor responsible for this three-week operation remains unknown.
“The exact group behind Operation Digital Eye remains unclear due to the extensive sharing of malware, operational playbooks, and infrastructure management processes within the Chinese threat landscape,” explains SentinelLabs.
Visual Studio Code backdoor
The hackers achieved initial access to the target systems using the automated SQL injection exploitation tool ‘sqlmap’ against internet-facing web and database servers.
Once they established access, they deployed a PHP-based webshell called PHPsert, which allowed them to execute commands remotely or introduce additional payloads.
For lateral movement, the attackers used RDP and pass-the-hash attacks, specifically, a custom version of Mimikatz (‘bK2o.exe’).
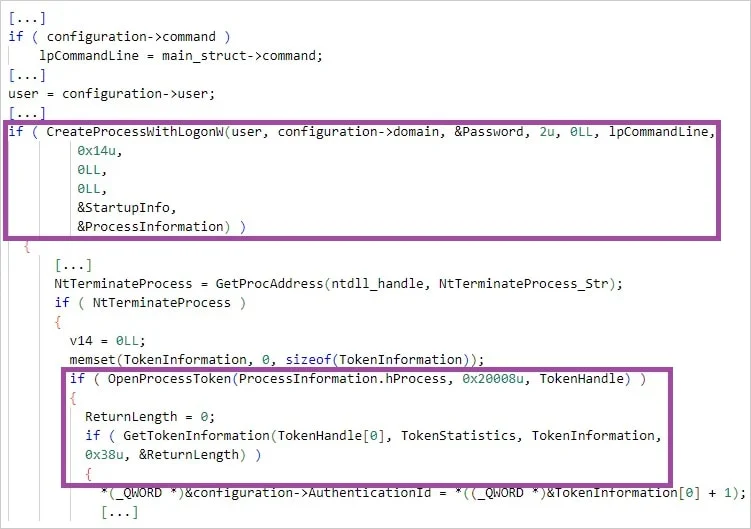
On breached devices, the hackers deployed a portable, legitimate version of Visual Studio Code (‘code.exe’) and used the ‘winsw’ tool to set it as a persistent Windows service.
Next, they configured VSCode with the tunnel parameter, enabling it to create a remote-access development tunnel on the machine.
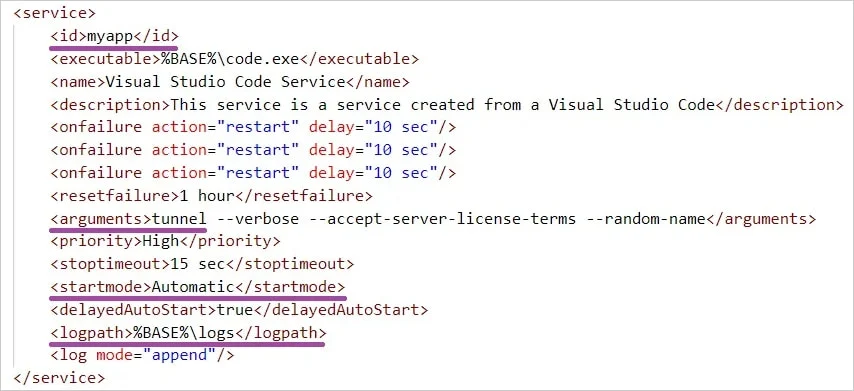
This enabled the threat actors to remotely connect to the breached device via a web interface (browser), authenticating with a GitHub or Microsoft account.
Because traffic to VSCode tunnels is routed through Microsoft Azure and all involved executables are signed, there’s nothing in the process to raise alarms by security tools.
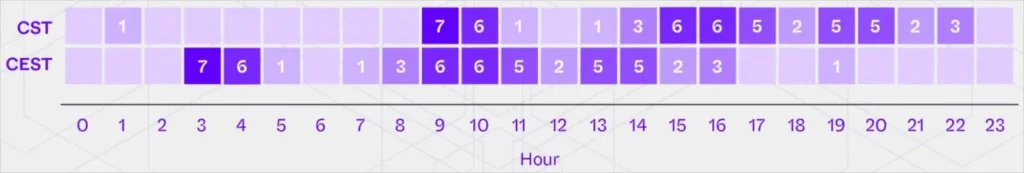
The threat actors used their VSCode backdoor to connect to the breached machines during workdays, showing high activity during standard working hours in China.
SentinelLabs says the use of VSCode tunnels isn’t unprecedented, as there have been some reports since 2023, however, it remains a rarely seen tactic.
In September 2024, Unit 42 published a report on the Chinese APT group ‘Stately Taurus’ abusing VSCode in espionage operations targeting government organizations in Southeast Asia. However, SentinelLabs says the two operations appear unrelated.
As the technique might be getting traction, defenders are advised to monitor for suspicious VSCode launches, limit the use of remote tunnels to authorized personnel, and use allowlisting to block the execution of portable files like code.exe.
Finally, it’s advisable to inspect Windows services for the presence of ‘code.exe,’ and look for unexpected outbound connections to domains like *.devtunnels.ms in network logs.



