
BootKitty UEFI malware exploits LogoFAIL to infect Linux systems
Update added below about this bootkit being created by students in Korea’s Best of the Best (BoB) cybersecurity training program.
The recently uncovered ‘Bootkitty’ Linux UEFI bootkit exploits the LogoFAIL flaw, tracked as CVE-2023-40238, to target computers running on vulnerable firmware.
This is confirmed by firmware security firm Binarly, which discovered LogoFAIL in November 2023 and warned about its potential to be used in actual attacks.
Bootkitty and LogoFAIL connection
Bootkitty was discovered by ESET, who published a report last week, noting that it is the first UEFI bootkit specifically targeting Linux. However, at this time, it is more of an in-development UEFI malware that only works on specific Ubuntu versions, rather than a widespread threat.
LogoFAIL is a set of flaws in the image-parsing code of UEFI firmware images used by various hardware vendors, exploitable by malicious images or logos planted on the EFI System Partition (ESP).
“When these images are parsed during boot, the vulnerability can be triggered and an attacker-controlled payload can arbitrarily be executed to hijack the execution flow and bypass security features like Secure Boot, including hardware-based Verified Boot mechanisms,” explained Binarly previously.
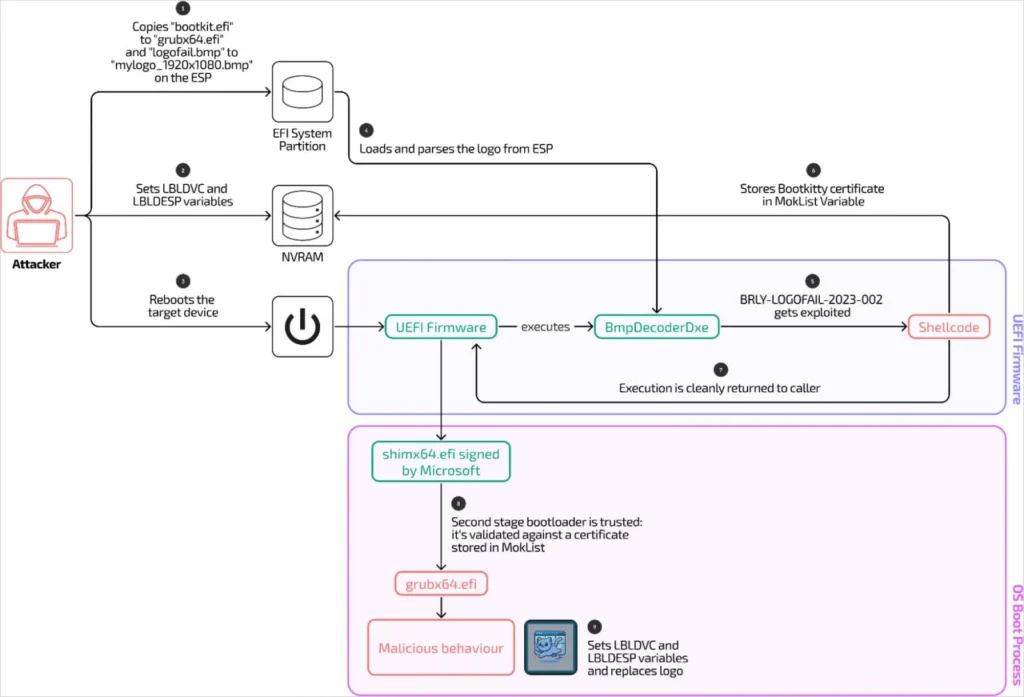
According to Binarly’s latest report, Bootkitty embeds shellcode within BMP files (‘logofail.bmp’ and ‘logofail_fake.bmp’) to bypass Secure Boot protections by injecting rogue certifications into the MokList variant.
The ‘logofail.bmp’ file embeds shellcode at its end, and a negative height value (0xfffffd00) triggers the out-of-bounds write vulnerability during parsing.
The legitimate MokList is replaced with a rogue certificate, effectively authorizing a malicious bootloader (‘bootkit.efi’).
After diverting execution to the shellcode, Bootkitty restores overwritten memory locations in the vulnerable function (RLE8ToBlt) with original instructions, so any signs of obvious tampering are erased.
Impact on specific hardware
Binarly says Bootkitty could impact any device that has not been patched against LogoFAIL, but its current shellcode expects specific code used in firmware modules found on Acer, HP, Fujitsu, and Lenovo computers.
The researcher’s analysis of the bootkit.efi file determined that Lenovo devices based on Insyde are the most susceptible, as Bootkitty references specific variable names and paths used by this brand. However, this could indicate that the developer is just testing the bootkit on their own laptop and will add support for a broader range of devices later.
Some widely used devices whose latest firmware is still vulnerable to LogoFAIL exploits include IdeaPad Pro 5-16IRH8, Lenovo IdeaPad 1-15IRU7, Lenovo Legion 7-16IAX7, Lenovo Legion Pro 5-16IRX8, and Lenovo Yoga 9-14IRP8.
“It’s been more than a year since we first sounded the alarm about LogoFAIL and yet, many affected parties remain vulnerable to one or more variants of the LogoFAIL vulnerabilities,” warns Binarly.
“Bootkitty serves as a stark reminder of the consequences of when these vulnerabilities are not adequately addressed or when fixes are not properly deployed to devices in the field.”
If you’re using a device with no available security updates to mitigate the LogoFAIL risk, limit physical access, enable Secure Boot, password-protect UEFI/BIOS settings, disable boot from external media, and only download firmware updates from the OEM’s official website.
Update 12/2/24: ESET updated their original BootKitty article today, stating that the project was created by cybersecurity students in Korea’s Best of the Best (BoB) training program.
“The primary aim of this project is to raise awareness within the security community about potential risks and to encourage proactive measures to prevent similar threats,” the program told ESET.
“Unfortunately, few bootkit samples were disclosed prior to the planned conference presentation.”



