
BadBox malware disrupted on 500K infected Android devices
The BadBox Android malware botnet has been disrupted again by removing 24 malicious apps from Google Play and sinkholing communications for half a million infected devices.
The BadBox botnet is a cyber-fraud operation targeting primarily low-cost Android-based devices like TV streaming boxes, tablets, smart TVs, and smartphones.
These devices either come pre-loaded with the BadBox malware from the manufacturer or are infected by malicious apps or firmware downloads.
The malware then turns the devices into residential proxies, generates fake ad impressions on the infected devices, redirects users to low-quality domains as part of fraudulent traffic distribution operations, and uses people’s IPs to create fake accounts and perform credential stuffing attacks.
Last December, German authorities disrupted the malware for infected devices in the country. However, a few days later, BitSight reported that the malware had been found in at least 192,000 devices, showing resilience against law enforcement action.
Since then, it is estimated that the botnet has grown to over 1,000,000 infections, impacting Android devices in 222 countries, with most located in Brazil (37.6%), the United States (18.2%), Mexico (6.3%), and Argentina (5.3%).
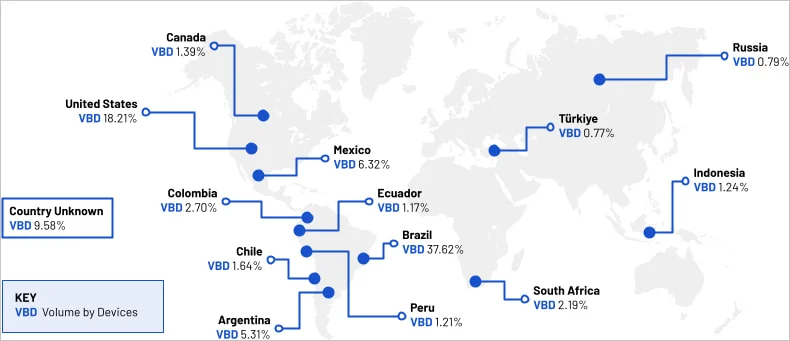
New BadBox disruption
HUMAN’s Satori Threat Intelligence team led the latest disruption operation in collaboration with Google, Trend Micro, The Shadowserver Foundation, and other partners.
Due to the botnet’s sudden size inflation, HUMAN now calls it ‘BadBox 2.0,’ indicating a new era in its operation.
“This scheme impacted more than 1 million consumer devices. Devices connected to the BADBOX 2.0 operation included lower-price-point, “off brand”, uncertified tablets, connected TV (CTV) boxes, digital projectors, and more,” explains HUMAN.
“The infected devices are Android Open Source Project devices, not Android TV OS devices or Play Protect certified Android devices. All of these devices are manufactured in mainland China and shipped globally; indeed, HUMAN observed BADBOX 2.0-associated traffic from 222 countries and territories worldwide.”
HUMAN says it found evidence that the botnet serves and is supported by multiple threat groups with distinct roles or benefits.
These groups are SalesTracker (infrastructure management), MoYu (backdoor and botnet development), Lemon (ad fraud campaigns), and LongTV (malicious app development).
Android devices infected with the BadBox malware will routinely connect to attacker-controlled command and control servers to receive new configuration settings and commands to execute on the infected device.
HUMAN told GeekFeed that, in partnership with The Shadowserver Foundation, the researchers sinkholed nearly a thousand BADBOX 2.0 domains to prevent over 500,000 infected devices from communicating with command-and-control (C2) servers set up by threat actors.
When a domain is sinkholed, it is take over by the researchers, allowing them to monitor all connections made by infected devices to that domain and gather data about the botnet. As the infected devices can no longer connect with attacker-controlled domains, the malware is put into a dormant state, effectively disrupting the infection.
HUMAN says it also discovered 24 Android apps in the official app store, Google Play, that installed the BadBox malware on Android devices. Some apps, like ‘Earn Extra Income’ and ‘Pregnancy Ovulation Calculator’ by Seekiny Studio, had over 50,000 downloads each.
Google removed the apps from Google Play and added a Play Protect enforcement rule to warn users and block the installation of apps associated with BadBox 2.0 on certified Android devices.
Moreover, the tech giant has terminated publisher accounts that engaged in ad fraud associated with the BadBox operation, preventing monetization through Google Ads.
However, it is important to note that Google cannot disinfect non-Play Protect-certified Android devices sold globally, so while BadBox 2.0 has been disrupted, it has not been eliminated.
Ultimately, as long as consumers buy AOSP-based Android devices like off-brand TV boxes, that lack official Google Play Services support, they are at risk of using hardware pre-loaded with malware.
A list of devices known to be impacted by the BadBox malware are listed below:
| Device Model | Device Model | Device Model | Device Model |
| TV98 | X96Q_Max_P | Q96L2 | X96Q2 |
| X96mini | S168 | ums512_1h10_Natv | X96_S400 |
| X96mini_RP | TX3mini | HY-001 | MX10PRO |
| X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
| X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
| X96QPRO-TM | sp7731e_1h10_native | M8SPROW | TV008 |
| X96Mini_5G | Q96MAX | Orbsmart_TR43 | Z6 |
| TVBOX | Smart | KM9PRO | A15 |
| Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
| X96Q | isinbox | Mbox | R11 |
| GameBox | KM6 | X96Max_Plus2 | TV007 |
| Q9 Stick | SP7731E | H6 | X88 |
| X98K | TXCZ |
In response to the disruption, Google shared the following statement with GeekFeed.
“We appreciate collaborating with HUMAN to take action against the BADBOX operation and protect consumers from fraud. The infected devices are Android Open Source Project devices, not Android TV OS devices or Play Protect certified Android devices,” says Shailesh Saini, Google’s Director of Android Security & Privacy Engineering & Assurance.
“If a device isn’t Play Protect certified, Google doesn’t have a record of security and compatibility test results. Play Protect certified Android devices undergo extensive testing to ensure quality and user safety. Users should ensure Google Play Protect, Android’s malware protection that is on by default on devices with Google Play Services, is enabled.”
If you own any of the above devices, it is likely that you will not be able to get clean firmware for them.
Instead, these devices should be replaced with those from reputable brands. If it is impossible to replace the device, they should be disconnected from the Internet.



