
CVE-2025-21298: A Critical Windows OLE Zero-Click Vulnerability
Explore CVE-2025-21298, a critical Windows OLE zero-click flaw enabling RCE via email. Learn its risks, impact, and how to defend against attacks.
In January 2025, a critical security vulnerability identified as CVE-2025-21298 was disclosed, affecting Windows Object Linking and Embedding (OLE) technology.
This vulnerability, with a CVSS score of 9.8, allows for remote code execution (RCE) through specially crafted emails, posing significant risks to users and organizations.
Understanding CVE-2025-21298
CVE-2025-21298 is a zero-click vulnerability in Windows OLE, a technology that enables embedding and linking to documents and other objects.
Attackers can exploit this flaw by sending a malicious email containing a harmful RTF document.
When the victim opens or previews the email in Microsoft Outlook, the vulnerability is triggered, allowing the attacker to execute arbitrary code on the affected system.
Technical Details
The vulnerability resides in the ole32.dll library, specifically within the `UtOlePresStmToContentsStm` function. This function is responsible for converting data in an “OlePres” stream within an OLE storage into appropriately formatted data and inserting it into the “CONTENTS” stream in the same storage.
A CVE-2025-21298 PoC has been made available on GitHub, demonstrating the memory corruption issue that leads to this vulnerability.
Reproducing the Attack
Open up a new word instance:
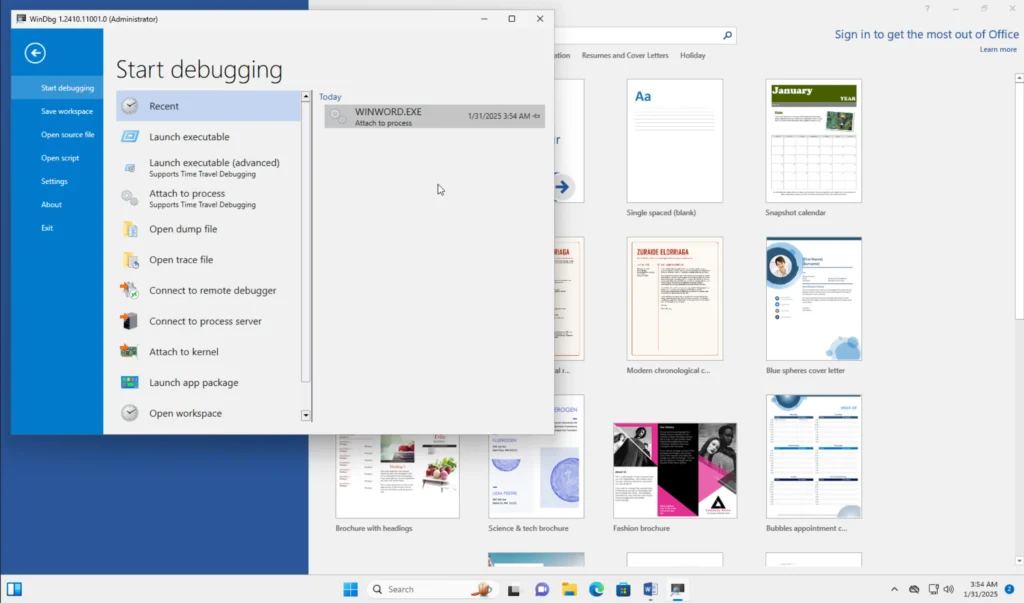
Attach WinDbg to the running WINWORD.EXE process:
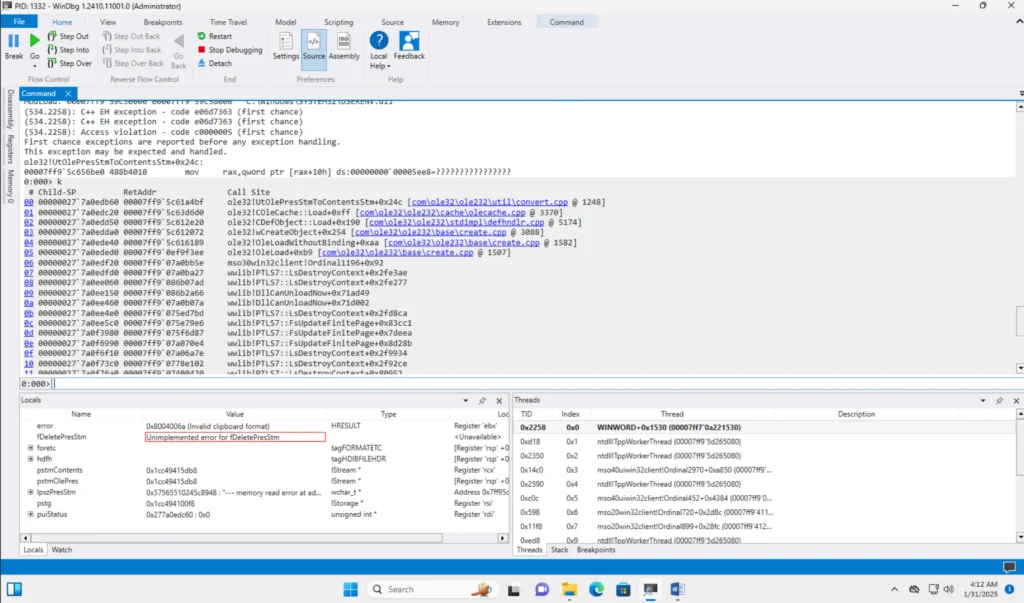
Open up the poc.rtf given in the repository and you will see WORD being crashed:
Impact
Upon successful exploitation, attackers can gain the same privileges as the current user, potentially leading to full system compromise.
This includes the ability to:
- Install programs
- View, change, or delete data
- Create new accounts with full user rights
The zero-click nature of this vulnerability means that exploitation can occur without any user interaction beyond opening or previewing the malicious email, inherently increasing its severity.
Mitigation and Recommendations
Microsoft has released patches to address this vulnerability as part of their January 2025 Patch Tuesday updates.
Users and organizations are strongly advised to apply these updates promptly to mitigate potential risks.
For those unable to update immediately, a recommended workaround is to configure Outlook to read all standard mail in plain text format, reducing the risk of automatic exploitation.
Detection and Defense
Security professionals can utilize detection rules to identify exploitation attempts of CVE-2025-21298.
For instance, Sigma rules are available to detect systems interacting with suspicious file types commonly associated with OLE exploitation, such as `.rtf` files.
Implementing these detection mechanisms can aid in early identification and response to potential attacks.
Conclusion
CVE-2025-21298 represents a significant security threat due to its high severity and the potential for remote code execution without user interaction.
Immediate action through patch application and the implementation of recommended workarounds is essential to protect systems from potential exploitation.
Continuous monitoring and the use of detection rules can further enhance an organization’s defense against such vulnerabilities.



