
‘Bitter’ cyberspies target defense orgs with new MiyaRAT malware
A cyberespionage threat group known as ‘Bitter’ was observed targeting defense organizations in Turkey using a novel malware family named MiyaRAT.
MiyaRAT is used alongside the WmRAT malware, which is cyberespionage malware previously associated with Bitter.
Proofpoint discovered the campaign and reports that the new malware is likely reserved for high-value targets, deployed only sporadically.
Bitter is a suspected South Asian cyberespionage threat group active since 2013, targeting government and critical organizations in Asia.
In 2022, they were spotted by Cisco Talos in attacks against the Bangladeshi government, using a remote code execution flaw in Microsoft Office to drop trojans.
Last year, Intezer reported that Bitter was impersonating the Embassy of Kyrgyzstan in Beijing in phishing attacks targeting various Chinese nuclear energy companies and academics.
Abusing alternate data streams
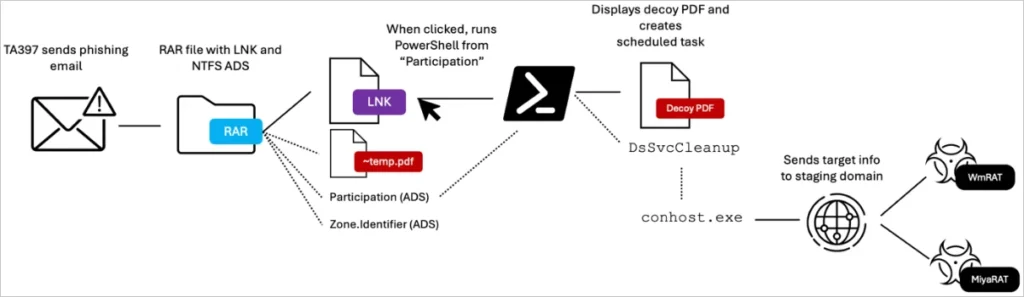
The attacks in Turkey started with an email containing a foreign investment project lure, attaching a RAR archive.
The archive contains a decoy PDF file (~tmp.pdf), a shortcut file disguised as a PDF (PUBLIC INVESTMENTS PROJECTS 2025.pdf.lnk), and alternate data streams (ADS) embedded in the RAR file named “Participation” and “Zone.Identifier.”
If the recipient opens the LNK file, they trigger the execution of PowerShell code hidden in the ADS, which opens the legitimate decoy PDF for distraction. At the same time, it creates a scheduled task named “DsSvcCleanup” that runs a malicious curl command every 17 minutes.
The command reaches a staging domain (jacknwoods[.]com) and awaits responses such as commands to download additional payloads, perform network reconnaissance, or steal data.
Proofpoint reports that a command to fetch WmRAT (anvrsa.msi) in the attack they examined was served within 12 hours.
The WmRAT and MiyaRAT malware
Bitter first deployed WmRAT on the target, but when it failed to establish communication with the command and control server, it downloaded MiyaRAT (gfxview.msi).
Both malware are C++ remote access trojans (RATs) that provide Bitter with data exfiltration, remote control, screenshot capturing, command execution (CMD or PowerShell), and system monitoring capabilities.
MiyaRAT is newer and generally more refined, featuring more advanced data and communications encryption, an interactive reverse shell, and enhanced directory and file control.
Its more selective deployment by Bitter may indicate that the threat actors reserve it for high-value targets, minimizing its exposure to analysts.
Indicators of compromise (IoCs) associated with this attack are listed at the bottom of Proofpoint’s report, while a YARA rule to help detect the threat is available here.



