
Clop ransomware claims responsibility for Cleo data theft attacks
The Clop ransomware gang has confirmed to GeekFeed that they are behind the recent Cleo data-theft attacks, utilizing zero-day exploits to breach corporate networks and steal data.
Cleo is the developer of the managed file transfer platforms Cleo Harmony, VLTrader, and LexiCom, which companies use to securely exchange files between their business partners and customers.
In October, Cleo fixed a vulnerability tracked as CVE-2024-50623 that allowed unrestricted file uploads and downloads, leading to remote code execution.
However, cybersecurity firm Huntress discovered last week that the original patch was incomplete and threat actors were actively exploiting a bypass to conduct data theft attacks.
While exploiting this vulnerability, the threat actors were uploading a JAVA backdoor that allowed the attackers to steal data, execute commands, and gain further access to the compromised network.
On Friday, CISA confirmed that the critical CVE-2024-50623 security vulnerability in Cleo Harmony, VLTrader, and LexiCom file transfer software has been exploited in ransomware attacks. However, Cleo never publicly disclosed that the original flaw they attempted to fix in October was exploited.
Clop claims responsibility for Cleo data theft attacks
It was previously thought that the Cleo attacks were conducted by a new ransomware gang named Termite. However, the Cleo data theft attacks tracked more closely to previous attacks conducted by the Clop ransomware gang.
After contacting Clop on Tuesday, the ransomware gang confirmed to GeekFeed that they are behind the recent exploitation of the Cleo vulnerability detected by Huntress as well as the exploitation of the original CVE-2024-50623 flaw fixed in October.
“As for CLEO, it was our project (including the previous cleo) – which was successfully completed.
All the information that we store, when working with it, we observe all security measures. If the data is government services, institutions, medicine, then we will immediately delete this data without hesitation (let me remind you about the last time when it was with moveit – all government data, medicine, clinics, data of scientific research at the state level were deleted), we comply with our regulations.
with love © CL0P^_”❖ Clop told GeekFeed
The extortion gang has now announced that they are deleting data associated with past attacks from their data leak server and will only work with new companies breached in the Cleo attacks.
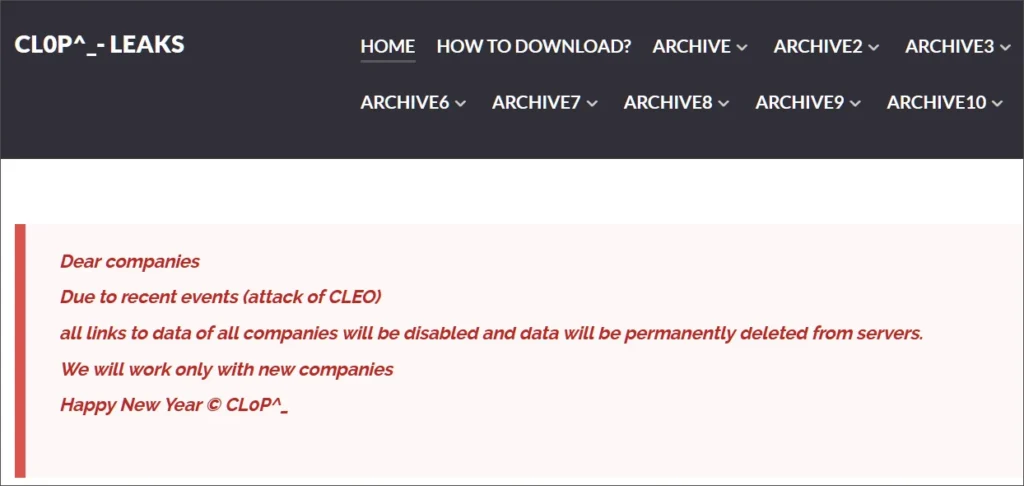
“Dear companies, Due to recent events (attack of CLEO) all links to data of all companies will be disabled and data will be permanently deleted from servers. We will work only with new companies,” reads a new message on the gang’s CL0P^_- LEAKS extortion site.
“Happy New Year © CL0P^_ all of the victims from their data leak site.”
GeekFeed asked Clop when the attacks began, how many companies were impacted, and if Clop was affiliated with the Termite ransomware gang, but did not receive a response to these questions.
GeekFeed also contacted Cleo on Friday to confirm if Clop was behind the exploitation of the vulnerabilities but did not receive a response.
Specializing in exploit file transfer platforms
The Clop ransomware gang, aka TA505 and Cl0p, launched in March 2019, when it first began targeting the enterprise using a variant of the CryptoMix ransomware.
Like other ransomware gangs, Clop breached corporate networks and slowly spread laterally through its systems while stealing data and documents. When they have harvested everything of value, they deployed ransomware on the network to encrypt its devices.
However, since 2020, the ransomware gang has specialized in targeting previously unknown vulnerabilities in secure file transfer platforms for data theft attacks.
In December 2020, Clop exploited a zero-day in the Accellion FTA secure file transfer platform, which impacted nearly one hundred organizations.
Then in 2021, the ransomware gang exploited a zero-day in SolarWinds Serv-U FTP software to steal data and breach networks.
In 2023, Clop exploited a zero-day in the GoAnywhere MFT platform, allowing the ransomware gang to steal data from over 100 companies again.
However, their most significant attack of this kind was using a zero-day in the MOVEit Transfer platform that allowed them to steal data from 2,773 organizations, according to a report by Emsisoft.
At this time, it is not clear how many companies have been impacted by the Cleo data theft attacks, and GeekFeed does not know of any companies who have confirmed being breached through the platform.
The U.S. State Department’s Rewards for Justice program currently has a $10 million bounty for information linking the Clop ransomware attacks to a foreign government.



