New Android spyware found on phone seized by Russian FSB
After a Russian programmer was detained by Russia’s Federal Security Service (FSB) for fifteen days and his phone confiscated, it was discovered that a new spyware was secretly installed on his device upon its return.
The programmer, Kirill Parubets, was arrested by the FSB after being accused of donating to Ukraine. After regaining access to his mobile device, the programmer suspected it was tampered with by the Russian government after it exhibited unusual behavior and displayed a notifications stating, “Arm cortex vx3 synchronization.”
After sharing it with Citizen Lab for forensic analysis, investigators confirmed that spyware had been installed on the device that impersonated a legitimate and popular Android app ‘Cube Call Recorder,’ which has over 10,000,000 downloads on Google Play.
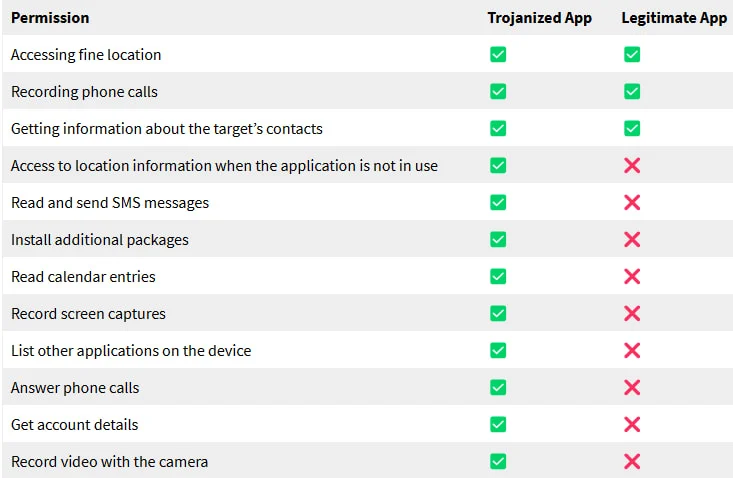
Contrary to the legitimate app, though, the spyware has access to a broad range of permissions, giving it unfettered access to the device and allowing the attackers to monitor the activities on the phone.
Citizen Lab reports that the malware appears to be a new version of Monokle, first discovered by Lookout in 2019, which is developed by the St Peterburg-based Special Technology Center, Ltd.
It’s also possible that the new malware discovered in Parubets’ device is a new tool that uses parts of Monokle code as its base.
“The many significant similarities in operations, functionality, and geopolitical motivations lead us to assess that this is either an updated version of the Monokle spyware or new software created by reusing much of the same code,” explains Citizen Lab.
The new spyware
The spyware implanted by FSB in the programmer’s phone uses an encrypted two-stage process that mirrors the architecture of the original Monokle but includes advancements in encryption and changes in its permissions.
Its capabilities include:
- Track location when idle
- Access SMS content, contacts list, and calendar entries
- Record phone calls, screen activity, and video (via the camera)
- Extract messages, files, and passwords
- Execute shell commands and decrypt data
- Perform keylogging to capture sensitive data and passwords
- Access messages from messaging apps
- Execute shell commands and install packages (APKs)
- Extract passwords stored on the device and also the device unlock password
- Exfiltrate files from the device
Citizen Labs notes that the second stage contains most of the spyware’s functionality and also includes encrypted files with seemingly random names to complicate detection.
The analysts also report finding references to iOS in the spyware’s code, which points to the possibility of a variant that runs on Apple iPhone devices.
Notable permission changes since the 2019 version (last documented) are the addition of ‘ACCESS_BACKGROUND_LOCATION’ and ‘INSTALL_PACKAGES’ and the removal of ‘USE_FINGERPRINT’ and ‘SET_WALLPAPER.’
People who have their device confiscated by law enforcement and later returned should switch to another device or hand it over to experts for analysis.
Those living in oppressive countries should consider using ‘burner’ devices when outside and at risk of arbitrary arrests, use anti-spyware mechanisms like Apple’s Lockdown mode, and keep the OS and apps up to date.



