
US offers $10M for tips on DPRK hacker linked to Maui ransomware attacks
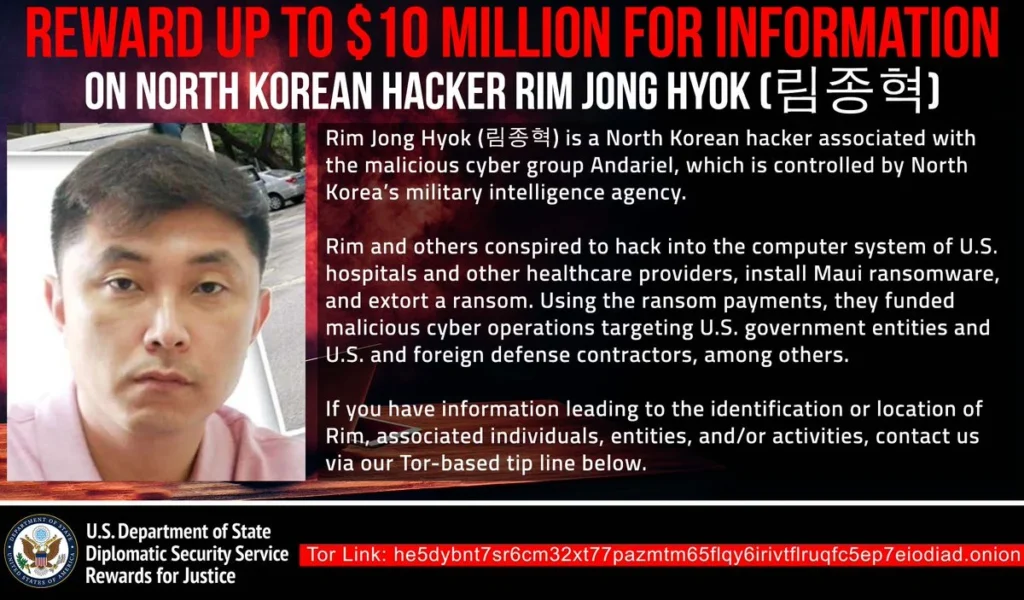
The U.S. State Department is offering a reward of up to $10 million for information that could help capture a North Korean military hacker identified as Rim Jong Hyok.
Part of the Andariel North Korean hacking group, Hyok and other Andariel operatives were linked to Maui ransomware attacks targeting critical infrastructure and healthcare organizations across the United States.
Hyok was charged with conspiracy to commit computer hacking and conspiracy to commit promotion money laundering, and a federal arrest warrant was issued in the U.S. District Court, District of Kansas, on Wednesday.
So far, U.S. law enforcement investigating their attacks has linked the North Korean hackers to ransomware incidents that impacted two U.S. Air Force bases, five healthcare providers, four U.S.-based defense contractors, and the National Aeronautics and Space Administration’s Office of Inspector General.
“Rim and others conspired to hack into the computer systems of U.S. hospitals and other healthcare providers, install Maui ransomware, and extort ransoms,” the State Department said.
“The ransomware attacks encrypted victims’ computers and servers used for medical testing or electronic medical records and disrupted healthcare services. These malicious cyber actors then used the ransom payments to fund malicious cyber operations targeting U.S. government entities and U.S. and foreign defense contractors, among others.”
In one such incident from November 2022, Andariel hackers breached the network of a U.S. defense contractor and stole more than 30 gigabytes of data, including unclassified information on military aircraft and satellites, much of it from 2010 or earlier.
These rewards are provided through the Rewards of Justice (RFJ) program, a U.S. Department of State program that offers rewards for information on threat actors targeting U.S. national security.
The State Department has also set up a dedicated Tor SecureDrop server to submit tips on Andariel hackers or other wanted threat groups and malicious actors.
Today, CISA and the FBI (in partnership with cybersecurity agencies from the United Kingdom and the Republic of Korea) also issued a joint advisory about this hacking group, which is tracked as APT45, Onyx Sleet, DarkSeoul, Silent Chollima, and Stonefly/Clasiopa and linked to North Korea’s Reconnaissance General Bureau (RGB) 3rd Bureau.
According to this advisory, Andariel is focused on stealing “sensitive military information and intellectual property of defense, aerospace, nuclear, and engineering organizations.”
“The information targeted—such as contract specifications, bills of materials, project details, design drawings, and engineering documents—has military and civilian applications and leads the authoring agencies to assess one of the group’s chief responsibilities as satisfying collection requirements for Pyongyang’s nuclear and defense programs,” the authoring agencies added.
This hacking group is believed to be an ongoing threat to a wide range of industry sectors worldwide, and all critical infrastructure organizations are advised to implement the mitigations recommended in today’s advisory.
On Thursday, Mandiant tagged Andariel/APT45 as one of North Korea’s longest-running cyber operations, dating back to 2009. In 2019, it targeted multiple nuclear power plants and research facilities, including India’s Kudankulam Nuclear Power Plant.



